This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.

sequal pentest, our penetration testing service for your information systems
This solution is in line with sequal’s core business, which is the support of its customers in the implementation of best practices in terms of information security, based on the ISO 27001 standard. Indeed, this standard addresses in point A.12.6.1 of its Annex A, the need to carry out pentests: Technical vulnerability management. And when we talk about IT security or more broadly about information systems, pentests naturally appear as an essential exercise to effectively test the robustness of a system.
Through this solution, sequal’s objective is to help its customers identify and correct possible security flaws in their information systems. The main goal is to prevent cybercriminals from damaging the confidentiality, integrity and availability of your data.

2 types of pentests
Periodic pentests
This type of pentest can be adapted if your information systems do not undergo any changes or regular updates, and you wish to test your security regularly.
Continuous Pentests
This type of pentesting is necessary if you develop your own application, for example. It will then be necessary to include pentests in the secure development cycle of your tool, especially before the release of major updates.
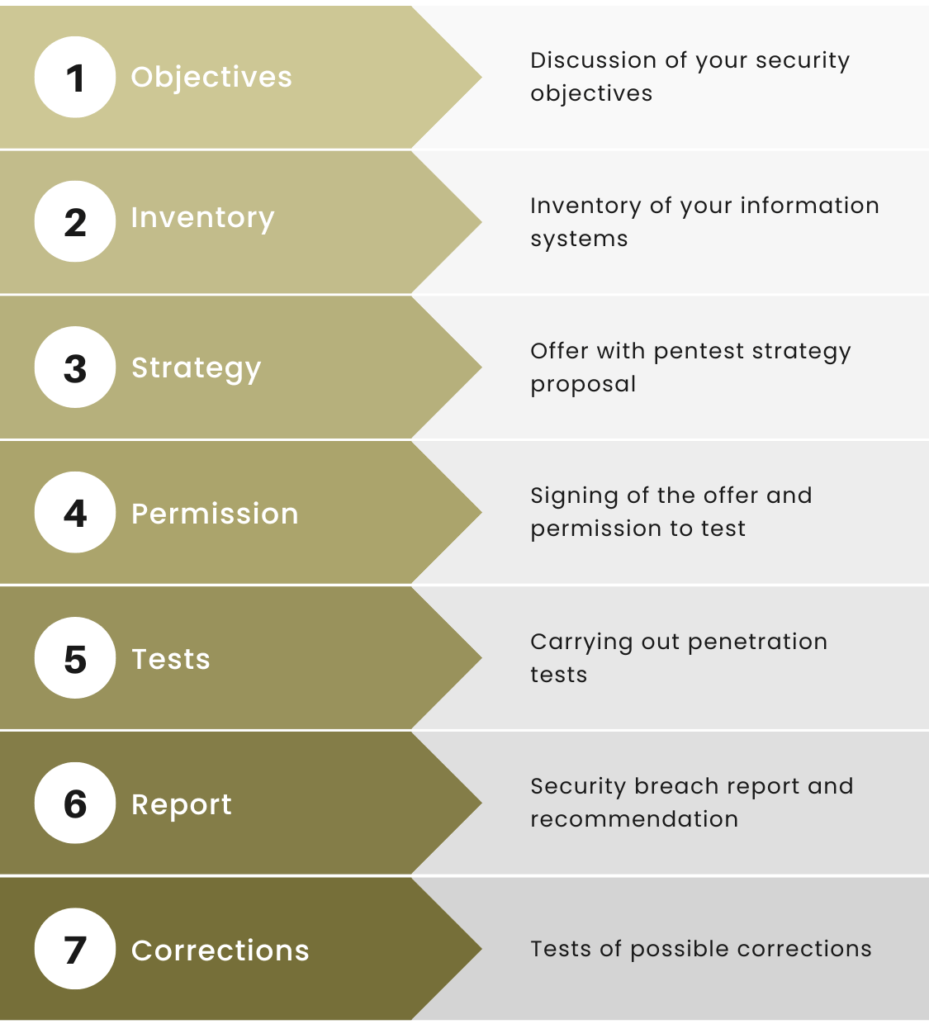
How do these pentests work?
The sequal pentest team
sequal pentest is the result of a collaboration between sequal and the HEIG-VD Competence Center for Computer Security, headed by Professor Sylvain Pasini, and his team from the HEIG-VD, notably Yann Lederrey, computer security engineer.
Do you have any questions
or would you like to test your information systems?





