ISO 27001
Do you process personal data that you can not afford to lose? Or information that you absolutely want to protect? This certification is for you!
As a first step, the organisation must identify the information which is absolutely necessary to protect, by its nature or value.
Secondly, the goal is to set up a framework and management tools around this information, i.e. an Information Security Management System (ISMS).
Contrary to what one might think, information security management is not limited to IT security, although very relevant in these times. It covers all areas related to the information and the management of its security:
- Security of human resources
- Risk management
- Access management, both physical and logical
- Security of the premises
- Compliance with all applicable laws and regulations
- Incident management
- Confirmed commitment of management, notably through the financial and human resources it allocates to information security, etc.
Why your organisation needs ISO/IEC 27001:2013 certification?
- Continuously improve the level of your information security
- Ensure that your employees are always trained and aware of information security issues
- Provide reasonable assurance on your level of security to your stakeholders (customers, suppliers, government, employees, etc.).
- Ensure your compliance with applicable laws and regulations
- Take advantage of ROSI (Return On Security Investment)
- Gain international recognition
Phishing
Training and awareness raising through click campaigns
Like everyone else, you’ve already become a millionaire according to that email you’ve received and all you had to do was click on a link. While it was obvious for you not to click, but what about your employees? Moreover, phishing emails are becoming more and more sophisticated, especially when the email address of the HR or the CEO have been imitated (Fake President).
The consequences are numerous and heavy when you think about a possible paralysis of your activities, but also about the blow to your reputation can take. We are talking about phishing, ransomware, data leakage or data theft.
Don’t waste any more time, get your entire organisation trained and tested continuously!
How to ensure this "continuous improvement"?
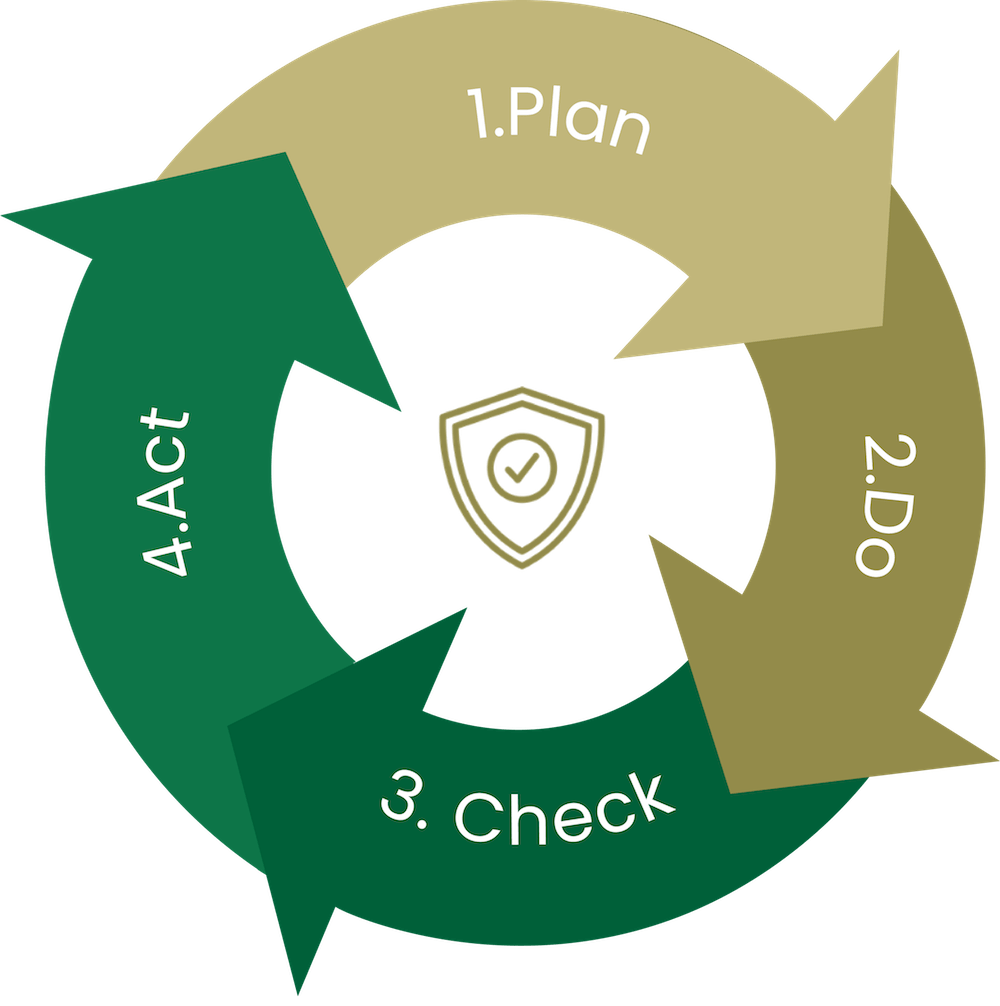
The foundation of continuous improvement, the PDCA (Plan – Do – Check – Act) is a widely used method for improving an organization’s performance in several areas (HR, Marketing, Logistics, etc.). It is also known as a virtuous circle. This method breaks down as follows:
- Plan: analysis of the situation, problem or issue at hand, search for and selection of solutions
- Do: implementation of the selected solution
- Check: measurement and evaluation of outcomes
- Act: implementation of the solution after any adjustments to the pilot solution